
Unlock the Future of Authentication
Protect your organization with next-gen passwordless authentication
Security Solutions Trusted by Leaders





Say Goodbye to Pa$$w0rds
of breaches are caused by
stolen credentials
Secure your workforce and customers with phishing-resistant MFA
Introducing Multi-Pass
Bolster security and delight your employees and customers with a seamless authentication experience.
Multi-Pass Pro
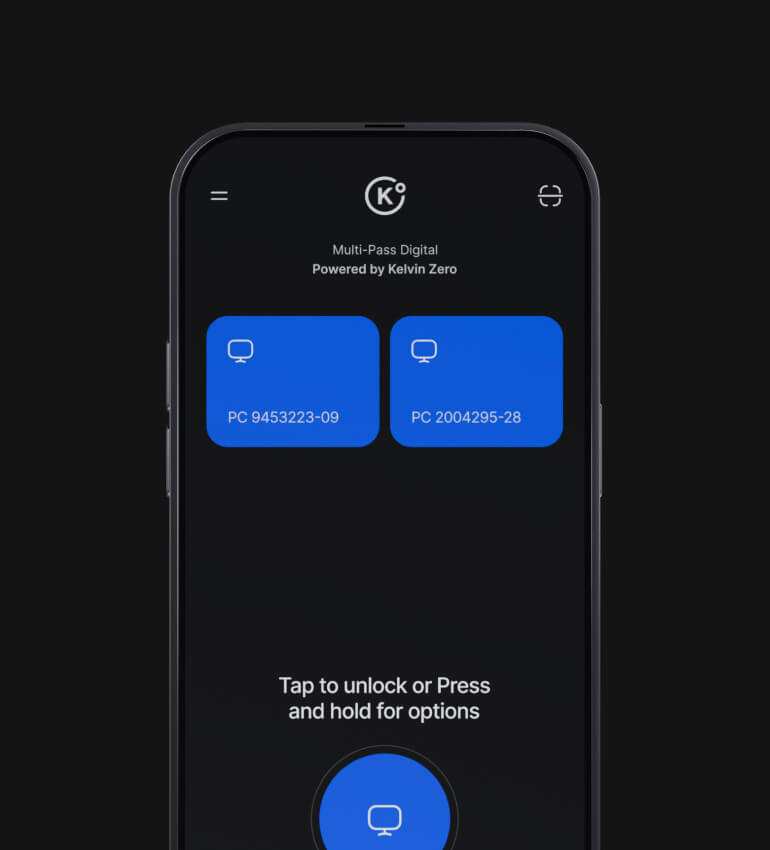
Multi-Pass Digital

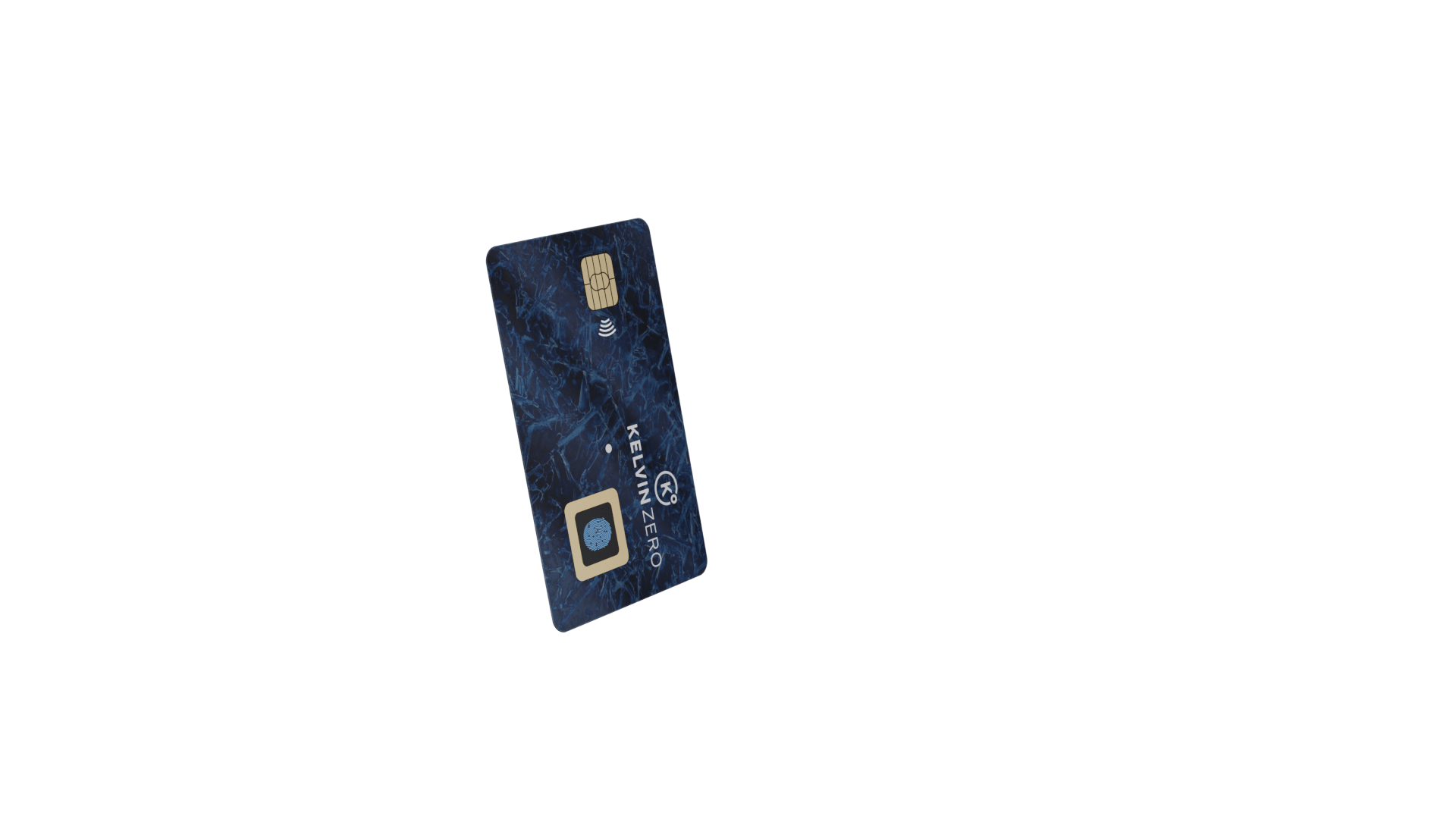
Multi-Pass Pro
Redefine authentication with a secure biometric pass.

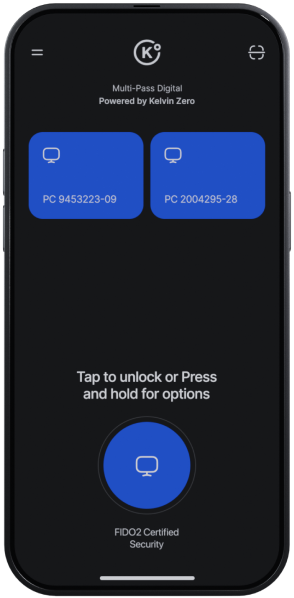
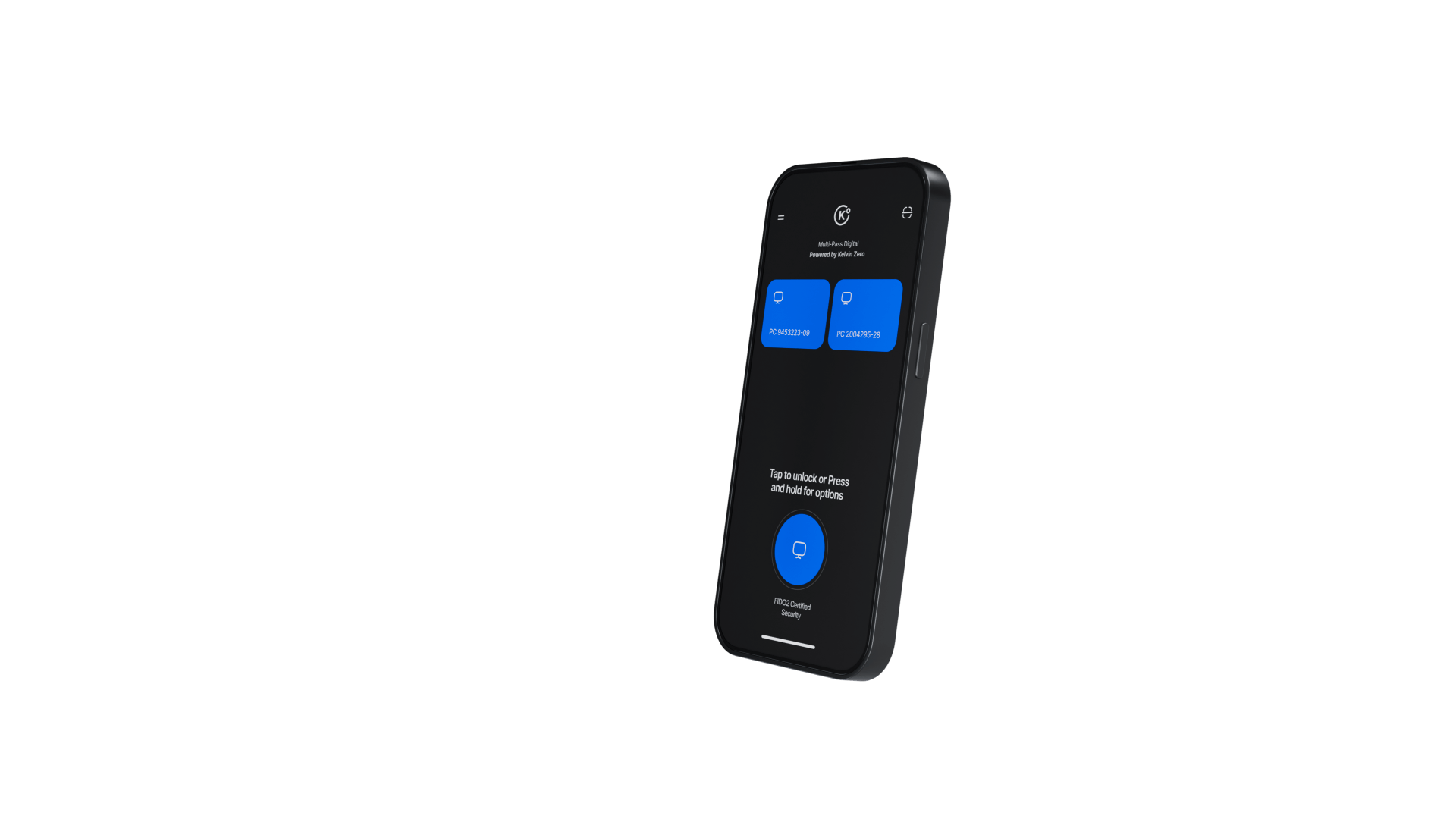
Multi-Pass Digital
Leverage biometrics on user mobile devices as a scalable enterprise passkey solution.
Enterprise passwordless solutions tailored to meet the security needs of all your users
Experience True Security

Deliver a secure and frictionless login experience
Meet and exceed stringent regulatory requirements

Reduce costs and free up IT resources

Future proof against new credential-based threats
Level Up with Passwordless MFA

Eliminate passwords and implement zero trust authentication with enterprise-grade FIDO2 certified software solutions.
Traditional Passwords
Multi-Device Passkeys
Password + Phishable MFA
Single-Device Enterprise Passkeys
Transform your mobile device into a FIDO2 passkey, eliminating passwords and shared secrets with secure asymmetric cryptography.
Next-Gen Authentication
The Fort Knox of Authentication.
Deliver the most robust security with offline-first authentication technology.
Keep keys off connected devices and offer an added layer of security against online threats.



Tamper-Proof Private Keys
The Power of Secure Element Technology
Keep your private keys safe in a securely housed tamper-resistant smart card chip. This is not just any chip, but a secure element built with the rigorous standards that protect the global financial system. Any attempt to compromise it? The keys are instantly destroyed, eliminating potential misuse.

Your Fingerprints, Your Privacy
With Multi-Pass Pro, only a non-reversible biometric fingerprint template is saved on the card and biometrics are never stored online or on the device.

Transform your smart phone into an external NFC reader
Login with any device using the Multi-Pass app and NFC reader feature. Access all enterprise resources with simple one-tap logins.
Integrate with your existing IdP and enable easy access to all your company resources
Workstation
Logins
Web Services
& Apps
Remote Work
Access
Physical
Access
Custom &
Legacy
How Multi-Pass Works
Frequently Asked Questions
Passwords come with inherent vulnerabilities due to the prevalence of weak passwords, password reuse, and social engineering attacks. But by using other systems such as biometrics or hardware signing devices, passwordless authentication provides a more secure and convenient way for users to authenticate themselves. This method eliminates the need for passwords and the associated risks, making it a popular choice for organizations looking to improve security, productivity, and user experience for their consumers and workforce.
Multi-Pass is a global access card and software solution that provides secure and convenient biometric authentication for users. It eliminates the need for passwords and time-consuming multi-step login experiences. Multi-Pass uses biometric technology to authenticate users: the smart card includes a fingerprint sensor and contactless technology to prove proximity and enable users to easily authenticate themselves with a single tap.
Multi-Pass improves security by eliminating the need for passwords, which can be easily guessed, stolen, or compromised. With biometric authentication built into each card, Multi-Pass ensures only authorized users can access sensitive information or systems. Multi-Pass provides a seamless method of authentication that is difficult to replicate or forge. This results in a more secure and convenient way for employees and customers to authenticate, reducing the risk of data breaches and unauthorized access.
Multi-Pass can be seamlessly integrated with your existing systems and workflows using the FIDO standard. If required, our team will work with you to understand your specific needs and ensure a smooth integration process. Multi-Pass can be customized to meet those unique needs, providing a flexible and adaptable authentication solution.
Ready to go Passwordless?
Schedule a Demo
Join Kelvin Zero
Help us create a safer digital world for everyone
We are growing fast and are looking for like-minded and ambitious people to join our team of world-class entrepreneurs and cybersecurity experts.